
Fashionable phishing kits marketed on cybercrime discussion boards as off-the-shelve packages element a number of, subtle detection avoidance and targeted traffic filtering techniques to guarantee that web stability solutions will not mark them as a threat.
Bogus sites that mimic nicely-known brands are considerable on the world wide web to lure victims and steal their payment particulars or account qualifications.
Most of these web-sites are built using phishing kits that aspect model logos, realistic login pages, and in cases of sophisticated offerings, dynamic webpages assembled from a set of standard things.
Risk actors use phishing kits thoroughly due to the automation they present, as they normally have to established up hundreds of pretend web pages every day to swap these detected and blocked the prior working day.
Nevertheless, that doesn’t necessarily mean that authors of these kits really don’t make an exertion to integrate anti-detection methods that would aid them keep up and managing for more time.
On the contrary, they are using a number of mechanisms to help maintain their destructive mother nature concealed from sophisticated danger detectors, and Kaspersky has revealed a report right now detailing the principal approaches.
How phishing kits keep concealed
1st, phishing kits consist of customer filtering settings that stop bots, assessment software, and guests from non-qualified destinations from moving into.
Lookup engine crawlers also have to be blocked from accessing the web page as placing it far too significant on research benefits increases the possibility of publicity and prospects to a prompt take-down.
Then there are the obfuscation solutions that intention to protect against detection from internet security equipment.
- Caesar cipher – Changing every character in the textual content by 1 that is a preset variety of positions even further down the alphabet so that the articles does not make feeling. When the website page is loaded, the shift reverts, and the accurate figures are exhibited.
- Web site resource encoding – AES or base64 encoding on the text or the page’s HTML code, which is much additional powerful than the Caesar technique. The written content is decoded on the browser when the website page is loaded.
- Invisible HTML tags – Include lots of junk HTML tags that are invisible when the web page is rendered on the browser and only serve as innocuous “noise” that hides the malicious sections.
- String slicing – Chopping strings into re-arrangeable groups of characters and referring to them by their quantity in a code desk. When the webpage is loaded, the strings are reassembled back into completion.
- Randomized HTML characteristics – Incorporating a big range of randomized tag attribute values to effectively disable anti-phishing instruments by rendering their guesses unreliable, which potential customers them to dismissal.
Some of the over tips are also used for obfuscating the stolen details from victims or the code of the phishing package to avoid unpaid copies and forks.
A shifting market
Kaspersky reports that in 2021, it detected 469 unique phishing kits supporting at minimum 1.2 million phishing internet websites.
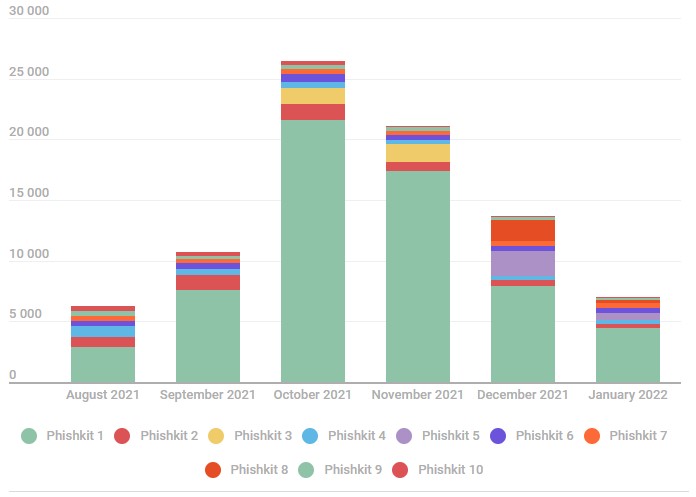
As the stability firm underlines, the range of sophisticated phishing kits that involve anti-bot, anti-detection, and geoblocking features consistently will increase.
The URLs to these web sites are circulated by way of emails, instantaneous messages, forum posts, and even YouTube films, so beware.




