
The Aberebot Android banking trojan has returned underneath the name ‘Escobar’ with new capabilities, which includes stealing Google Authenticator multi-issue authentication codes.
The new capabilities in the most up-to-date Aberebot edition also include things like getting regulate of the contaminated Android units working with VNC, recording audio, and having images, whilst also increasing the established of specific apps for credential theft.
The primary goal of the trojan is to steal sufficient details to let the risk actors to acquire above victims’ financial institution accounts, siphon available balances, and conduct unauthorized transactions.
Rebranded as Escobar
Working with KELA‘s cyber-intelligence DARKBEAST platform, BleepingComputer found a discussion board publish on a Russian-speaking hacking discussion board from February 2022 where the Aberebot developer promotes their new model underneath the title ‘Escobar Bot Android Banking Trojan.’
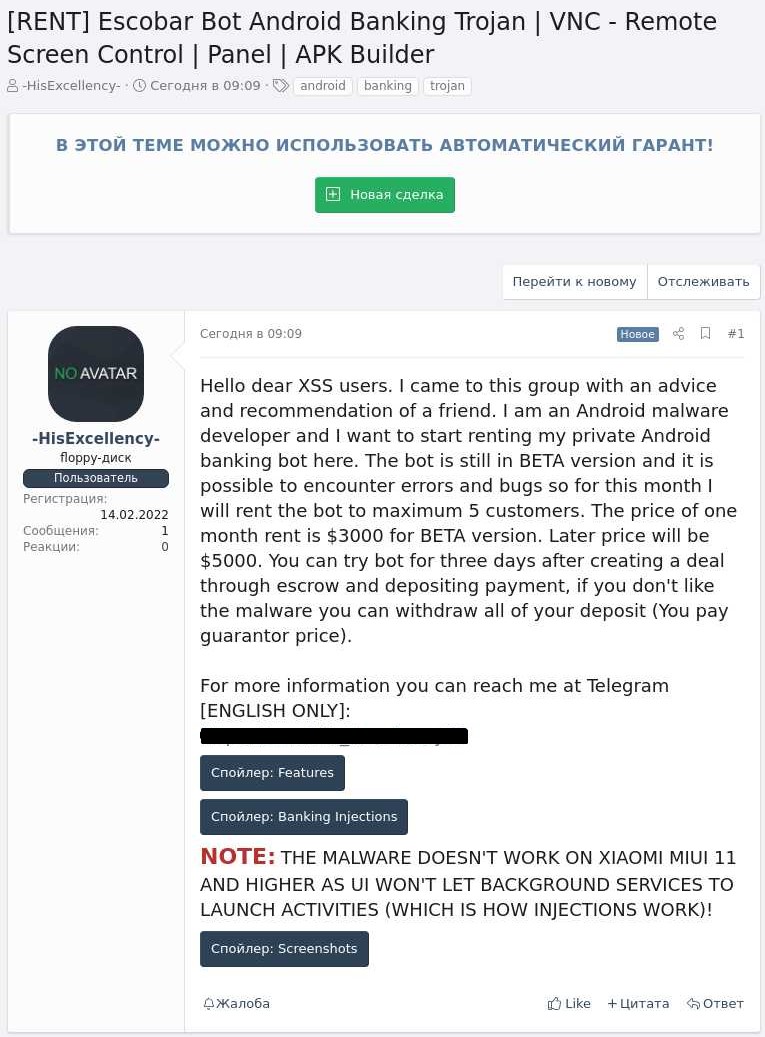
The malware author is leasing the beta version of the malware for $3,000 for every thirty day period to a maximum of 5 consumers, with risk actors acquiring the means to test the bot for free for three times.
The menace actor plans on raising the malware’s cost to $5,000 soon after improvement is finished.
MalwareHunterTeam 1st spotted the suspicious APK on March 3, 2022, masqueraded as a McAfee app, and warned about its stealthiness from the broad vast majority of anti-virus engines.
Probable appealing, extremely very low detected “McAfee9412.apk”: a9d1561ed0d23a5473d68069337e2f8e7862f7b72b74251eb63ccc883ba9459f
From: https://cdn.discordapp[.]com/attachments/900818589068689461/948690034867986462/McAfee9412.apk
“com.escobar.pablo”
pic.twitter.com/QR89LV4jat— MalwareHunterTeam (@malwrhunterteam) March 3, 2022
This was picked up by scientists at Cyble, who done an analysis of the new ‘Escobar’ variant of the Aberebot trojan.
According to the very same analysts, Aberebot initially appeared in the wild in the summer months of 2021, so the overall look of a new version suggests lively improvement.
Aged and new abilities
Like most banking trojans, Escobar shows overlay login forms to hijack user interactions with e-banking applications and web sites and steal qualifications from victims.
The malware also packs many other features that make it powerful in opposition to any Android edition, even if the overlay injections are blocked in some manner.
The authors have expanded the established of targeted banking companies and monetary institutions to a whopping 190 entities from 18 nations in the hottest version.
The malware requests 25 permissions, of which 15 are abused for destructive applications. Examples contain accessibility, audio record, study SMS, read through/ write storage, get account listing, disabling the keylock, generating phone calls, and accessing precise product place.
Anything that the malware collects is uploaded to the C2 server, which include SMS contact logs, essential logs, notifications, and Google Authenticator codes.
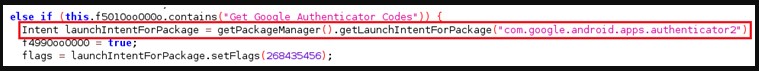
The over is plenty of to assist the crooks defeat two-issue authentication obstacles when assuming manage of e-banking accounts.
2FA codes get there by way of SMS or are stored and rotated in HMAC software package-dependent equipment like Google’s Authenticator. The latter is regarded as safer thanks to not being vulnerable to SIM swap assaults, but it’s nevertheless not guarded from malware infiltrating the userspace.
Furthermore, the addition of VNC Viewer, a cross-platform monitor sharing utility with distant regulate functions, gives the menace actors a new impressive weapon to do whatever they want when the machine is unattended.
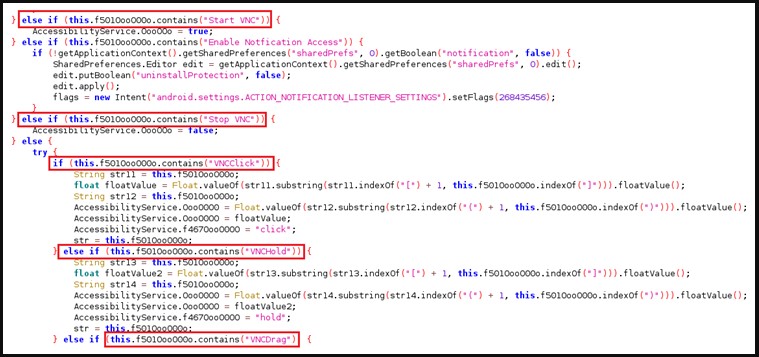
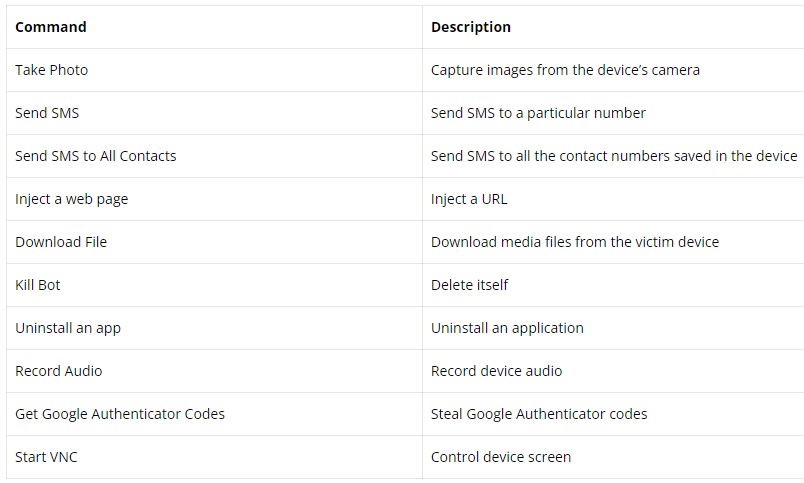
Apart from the earlier mentioned, Aberebot can also record audio clips or choose screenshots and exfiltrate equally to the actor-controlled C2, with the complete checklist of supported commands shown below.
Must we be anxious?
It is nevertheless early to convey to how common the new Escobar malware will turn out to be in the cybercrime neighborhood, specially at a rather higher selling price. However, it can be now potent ample to entice a wider viewers.
Also, its operational model, which involves random actors that can lease it, means its distribution channels and procedures may possibly change tremendously.
In general, you can reduce the odds of staying contaminated with Android trojans by avoiding the set up of APKs outside of Google Perform, applying a cellular security resource, and guaranteeing that Google Perform Protect is enabled on your gadget.
Furthermore, when setting up a new app from any source, fork out notice to strange requests for permissions and keep track of the app’s battery and network intake stats for the initially number of times to recognize any suspicious styles.






